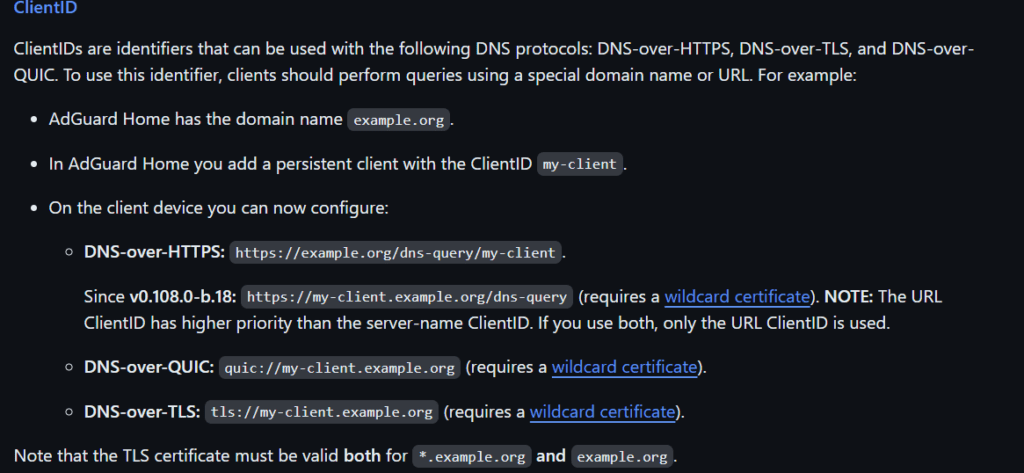
I installed a mini BOSGAME computer that was enough for speed internet and the performance was excellent with a multiserver firewall. Furthermore, I have also installed WireGuard VPN on the firewall to enable remote access to my server from a single IP address. I won’t get attacked or hacked from ssh.
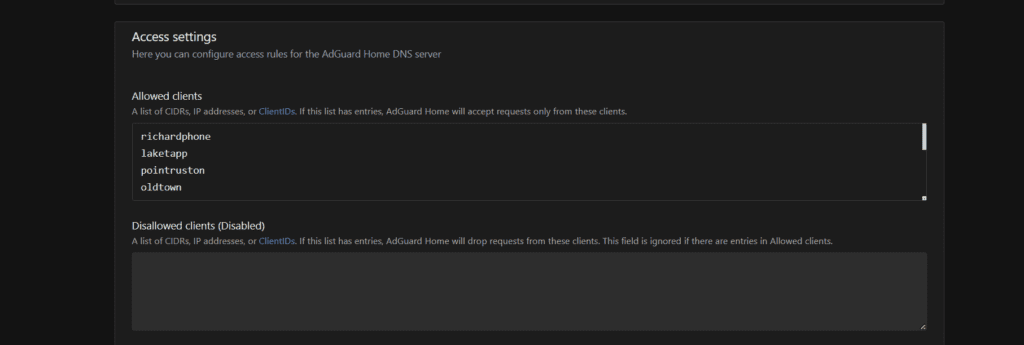
Firewall to protect our server to avoid any hacking, malware, ransomware and more… Our firewall had Phishing Blocker and spam blocker for our Email server. Very benefits for our business.
I also like bandwidth control for our server to improve performance.

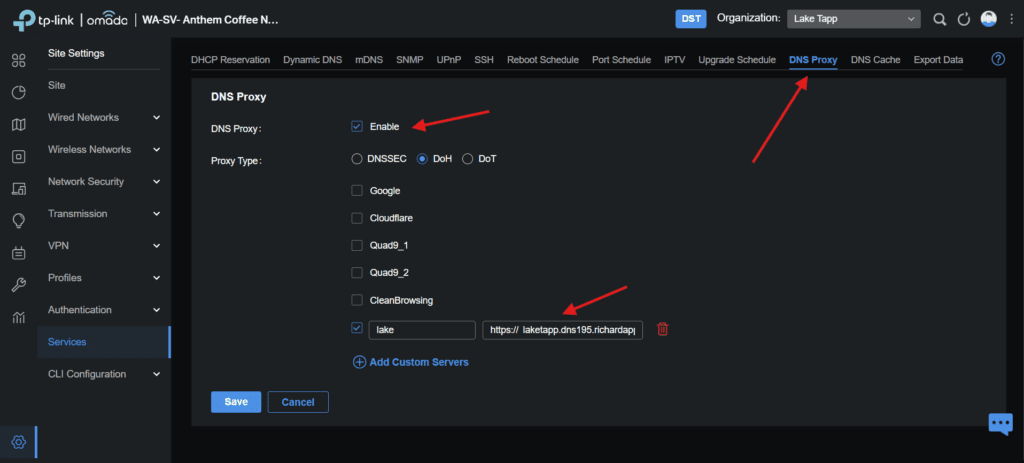
Testing Speed Test with WireGuard with mini PC.
With WireGuard VPN
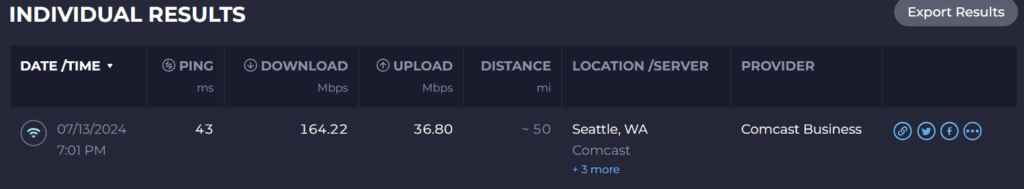
without VPN
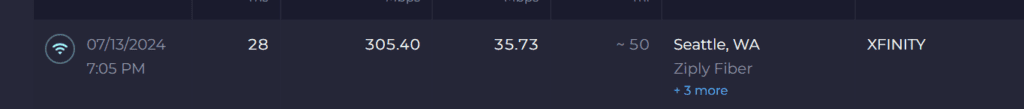
I am happy with the speed because I had Server at location was 600mbps download and 200 uploads from Comcast business. So My firewall can handle VPN and firewall and many features. Now our Server and Web hosting is safe again. My home is 300 and 35 from Xfinity, So My Upload is perfect.
Firewall Hardware Specific
This pretty good to handle our server. 🙂
| Brand | BOSGAME |
|---|---|
| Series | MINI PC |
| Item model number | E1 |
| Operating System | Windows 11 Pro |
| Item Weight | 1.83 pounds |
| Product Dimensions | 4.96 x 4.41 x 1.61 inches |
| Item Dimensions LxWxH | 4.96 x 4.41 x 1.61 inches |
| Color | Black |
| Processor Brand | Intel |
| Number of Processors | 4 |
| Computer Memory Type | DDR4 SDRAM |
| Flash Memory Size | 16 GB |
| Hard Drive Interface | PCIE x 2 |
| Standing screen display size | 75 |
|---|---|
| Screen Resolution | 3840 x 2160 |
| Max Screen Resolution | 3840 x 2160 pixels |
| Processor | 3.4 GHz Celeron |
| RAM | 16 DDR4 |
| Hard Drive | 512 GB SSD |
| Graphics Coprocessor | Intel UHD Graphics |
| Chipset Brand | Intel |
| Card Description | Integrated |
| Graphics Card Ram Size | 16 GB |
| Number of USB 3.0 Ports | 4 |
https://www.amazon.com/BOSGAME-E1-Windows-Computer-Supports/dp/B0CSK4C2ZR
I also Did PC to Smaller PC because it can fit in Cabinet network to secure.