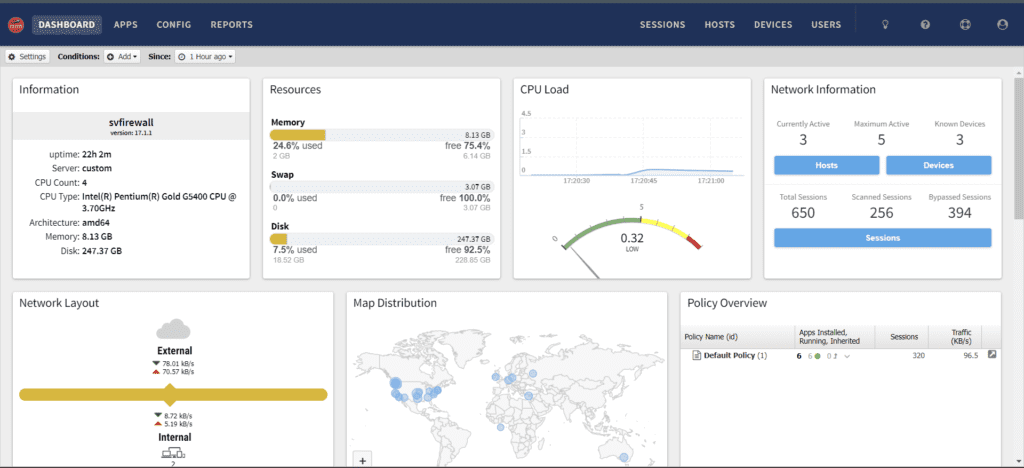
I built another mini computer for Sunrise Village and added another network card to my mini computer for internal and external network. Not only that, but I also set Internal to “bridge” and set my Modem wire to firewall “external” and then firewall “internal” to a 1 gigabit switch. So I can put more Server in one 1gig switch. We had static IP, and we’re using these on our server, so My Firewall will not protect my server until I create rules and firewall and Threat Prevention and virus Blocker.
We can upgrade to 2.5Gig or 10gig speed on our server and firewall, but our plans are 600mbps and 200mbps uploads, so it is enough for all my server to hosting on switch.
Not only that, but we have Three locations that require a firewall. I set up a firewall at Sunrise Village a few days ago, and it is working well. We need to protect where our server is that runs all of our store network and slack alternative and cloud storage.
User 1: Omada TpLink Router Hosting
User 2: Web and Email Hosting
User 3: all apps in one server solution.
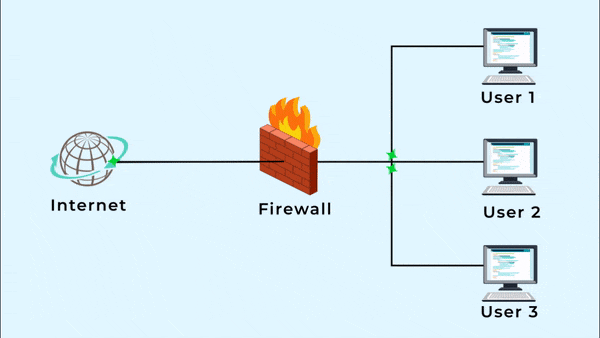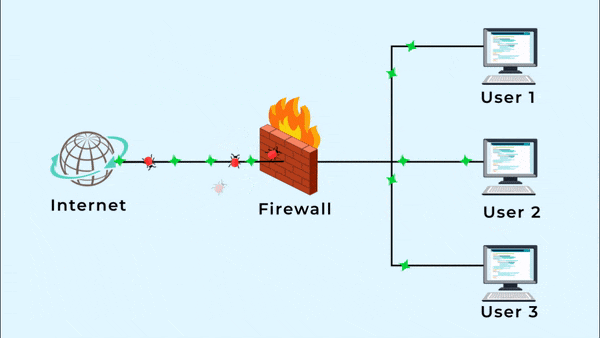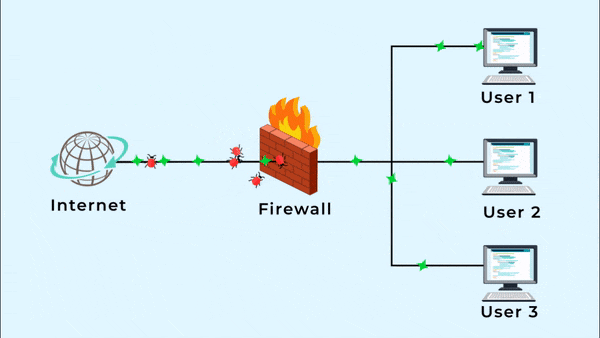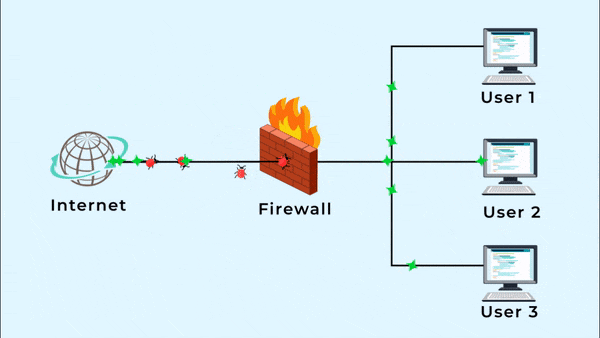
A firewall serves as a safeguard against distributed denial-of-service attacks on the Internet.
The firewall on our modem is weak, and we’re still getting DDoS attacks. We need a better firewall, so we can’t worry about our server and network systems.